Keycloak is a leading open source solution in the cloud-native ecosystem for Identity and Access Management, a key component of accessing applications and their data.
With the release of Keycloak 26.4, we’ve added features for both machine and human identities. New features focus on security enhancement, deeper integration, and improved server administration. See below for the release highlights, or dive deeper in our Keycloak 26.4 release announcement.
Keycloak recently surpassed 30k GitHub stars and 1,350 contributors. If you’re attending KubeCon + CloudNativeCon North America in Atlanta, stop by and say hi—we’d love to hear how you’re using Keycloak!
What’s New in 26.4
Passwordless user authentication with Passkeys
Keycloak now offers full support for Passkeys. As secure, passwordless authentication becomes the new standard, we’ve made passkeys simple to configure. For environments that are unable to adopt passkeys, Keycloak continues to support OTP and recovery codes. You can find a passkey walkthrough on the Keycloak blog.
Tightened OpenID Connect security with FAPI 2 and DPoP
Keycloak 26.4 implements the Financial-grade API (FAPI) 2.0 standard, ensuring strong security best practices. This includes support for Demonstrating Proof-of-Possession (DPoP), which is a safer way to handle tokens in public OpenID Connect clients.
Simplified deployments across multiple availability zones
Deployment across multiple availability zones or data centers is simplified in 26.4:
- Split-brain detection
- Full support in the Keycloak Operator
- Latency optimizations when Keycloak nodes run in different data centers
Keycloak docs contain a full step-by-step guide, and we published a blog post on how to scale to 2,000 logins/sec and 10,000 token refreshes/sec.
Authenticating applications with Kubernetes service account tokens or SPIFFE
When applications interact with Keycloak around OpenID Connect, each confidential server-side application needs credentials. This usually comes with the churn to distribute and rotate them regularly.
With 26.4, you can use Kubernetes service account tokens, which are automatically distributed to each Pod when running on Kubernetes. This removes the need to distribute and rotate an extra pair of credentials. For use cases inside and outside Kubernetes, you can also use SPIFFE.
To test this preview feature:
- Enable the features
client-auth-federated:v1,spiffe:v1, andkubernetes-service-accounts:v1. - Register a Kubernetes or SPIFFE identity provider in Keycloak.
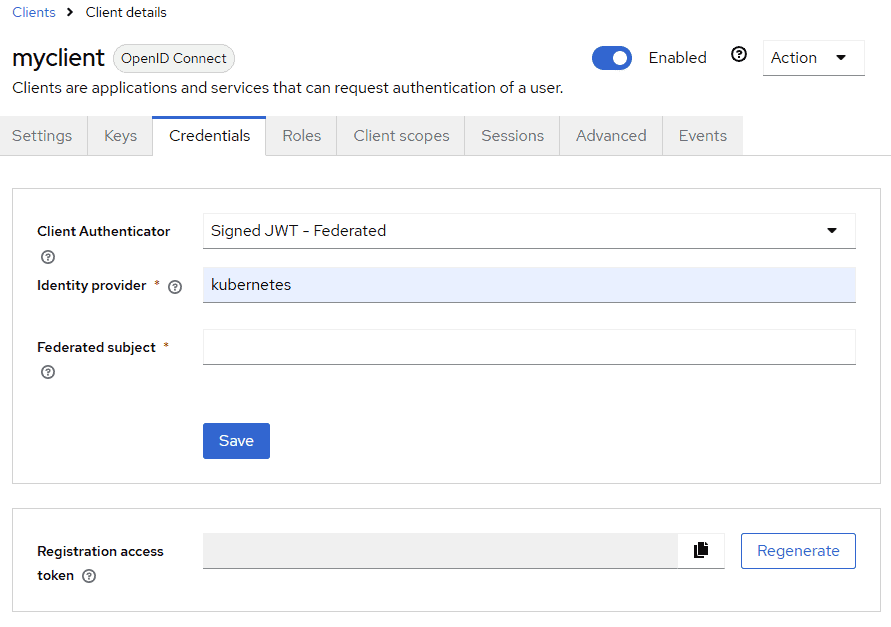
- For a client registered in Keycloak, configure the Client Authenticator in the Credentials tab as Signed JWT – Federated, referencing the identity provider created in the previous step and the expected subject in the JWT.
Looking ahead
Keycloak’s roadmap includes:
- Improved MCP support to better support AI agents
- Improved token exchange
- Automating administrative tasks using workflows triggered by authentication events.
You can follow our journey at keycloak.org and get involved. Our nightly builds give you early access to Keycloak’s latest features.