
Zero Downtime, Maximum Trust: How Infosys Built Unbreakable Infrastructure for a Fortune 100 Financial Giant
Challenge
The organization needed a highly scalable NAV calculation system integrating multiple applications in a regulated environment with strict security, availability, and observability requirements. The solution required breaking down decades-old silos, ensuring data separation, enabling faster upgrades, and enforcing multi-layered security.
Solution
The team implemented Istio service mesh on OpenShift with multi-layered security using Azure AD authentication, JWT token validation, and ingress gateway protection. They used Istio’s traffic management with autoscaling and observability through Kiali, Jaeger, ELK stack, and AppDynamics.
Impact
The application eliminated decades-old silos, processed billions of dollars without failures, and achieved 40% increases in efficiency and operational cost savings. The in-house application became a product securing $300 million in deals, generating 10x more revenue with zero security incidents.
By the numbers
300M USD
Generated in revenue
AT least 40%
reduction in operational expenses
0%
unauthorized access to the system since implementation
Breaking Down Decades-Old Silos in a Regulated Environment
A large, global financial services organization developed a system to calculate NAV (Net Asset Value) by integrating it with their existing internal and external systems. Operating in a highly regulated and tightly controlled environment, the application complied with strict requirements for availability, security, and observability. This solution helped the bank reduce operational costs, enhance system availability, productize the application, and generate additional revenue.
Designing and developing within the constraints of the client’s existing infrastructure presented a significant challenge, while interfacing with their application suite introduced additional complexities.
The team needed to design and develop a highly scalable application with multiple upstream and downstream applications with seamless interoperability. Due to the global nature of operations and changing regulatory requirements and frequent software upgrades, there was a need to upgrade systems faster, bug-free, and in a phased manner.
The requirement was to have clear separation of data and not allow any data copy or data duplication between bounded contexts. Security being one of the pillars of this program, maintaining and enforcing security from every aspect, including authentication, authorization, secure access to data, and access to third-party apps, required thoughtful design and checks and balances across multiple layers.
Multi-Layered Security Architecture with Istio
The team approached the solution comprehensively. The client already had a private cloud setup in OpenShift. Azure AD handles authentication of internal users. Since this application is accessed only by internal users of the organization, separate registration was not required.
Internal users of the app have custom fine-grained authorization implemented so they have access to do more things in the app than the other users of the organization. The team implemented a service mesh solution to take care of authentication, authorization, traffic routing, A/B testing, etc. All external hosts other than authorized are blocked at service mesh boundary level using ingress gateway. All fine-grained custom authorization which the customer wanted to implement was bundled as Jar and deployed in the control plane.
A token service was implemented to issue JWT tokens with necessary permissions post AD Authentication. Istio authorization policy was implemented to validate the authenticity of requests by parsing the incoming JWT tokens in every sidecar of every pod. So apart from firewall and other network level protection, there were multiple layers of protection in ingress gateway, Azure AD, and Sidecar using JWT. This robust security implementation helped protect the application from inadvertent access.
Traffic Management at Scale
The team implemented Istio’s VirtualService and DestinationRule to specify routing and route traffic to specific destinations and versions of pods. By combining load-based traffic routing with autoscaling, the system processes large volumes of heavy traffic without any delay or failure. Health checks are implemented at the pod level to ensure application resilience. This approach enables efficient traffic routing and ensures isolated containers are always available for A/B testing and blue/green deployment.
An egress gateway routes traffic outside of the mesh. The team uses Istio’s Kiali dashboard to view application traffic in real-time through a graphical UI. Fine-grained API traffic is available through Jaeger integration. The implementation also includes ELK stack to inject logs into Elasticsearch and view them in Kibana dashboards. AppDynamics agents were added to each container to collect metrics and generate custom rule alerts. These combined implementations deliver robust observability with a highly secure app and multiple layers of control.
There are plans to deploy AI agents to auto-heal applications as an extra precaution. AI agents are used in software upgrades.
Note: This implementation was done just before the release of ambient mesh and the later developments in kernel programming like eBPF. This solution if implemented today can be simplified by introducing ambient mesh instead of sidecar pattern or doing eBPF-based implementation to remove the overheads.
Solution Architecture
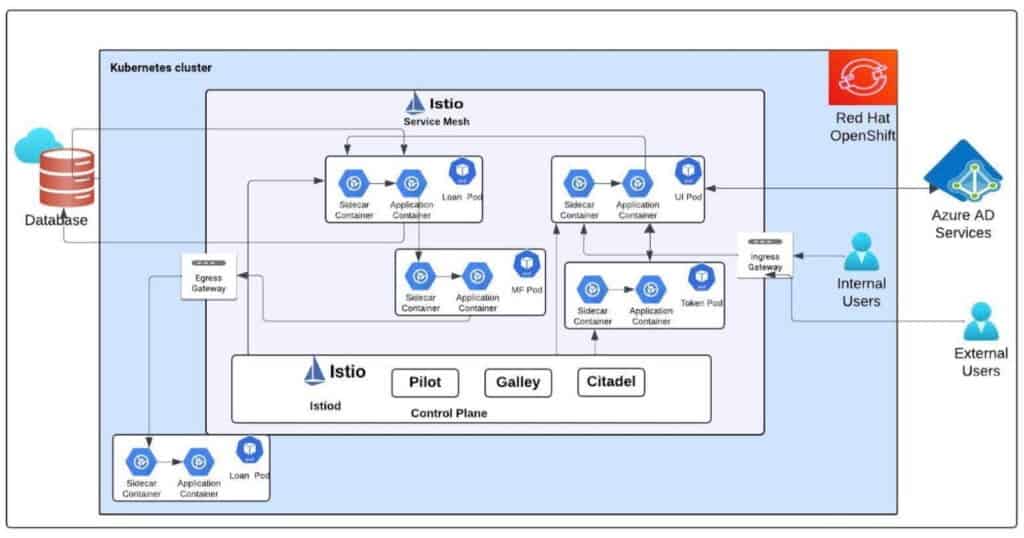
Key Use Cases
Security
- The team implemented security across various layers, starting with the ingress gateway layer to block any unknown hosts.
- Azure AD authentication blocks unauthorized user access and issues JWT tokens to authenticated users.
- Client custom authorization is implemented in the control plane to uniformly apply across all pods.
- Istio’s authorization policy combined with JWT tokens at the pod level ensures robust security across multiple layers.
Security Flow
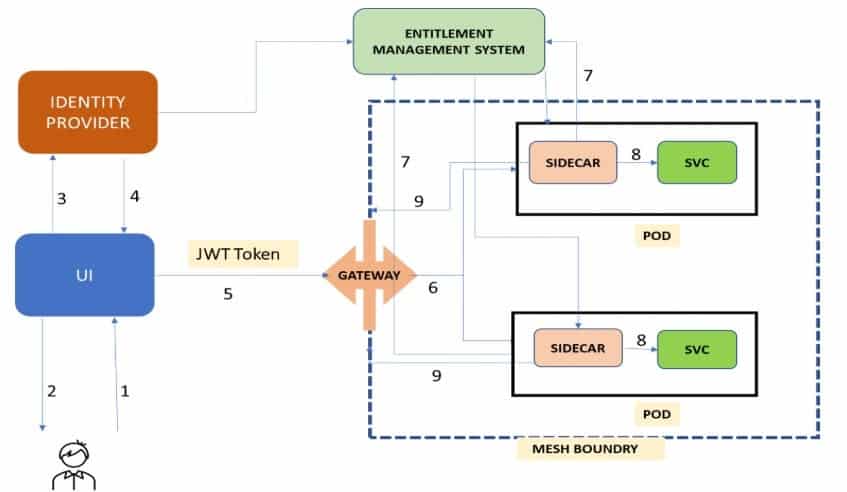
- Users access the web URL through their browser
- The user is presented with an SSO login page to enter their credentials
- The identity provider validates the credentials and retrieves the user’s role from EEM
- The identity provider generates a JWT token with TTL (time to live) and the user’s role appended in JWT payload claims
- The JWT token is passed in the session header and the request is routed to the Ingress Gateway
- The gateway validates the JWT token validity and claim presence, then forwards the request to the sidecar container of the pod
- The sidecar container validates the user’s entitlement for the particular API and service in EEMS using the role from JWT claims
- Only requests with valid entitlement are routed to the service
- If the user lacks entitlement, they are routed back to the UI page with a valid error message
High Availability and Scalability
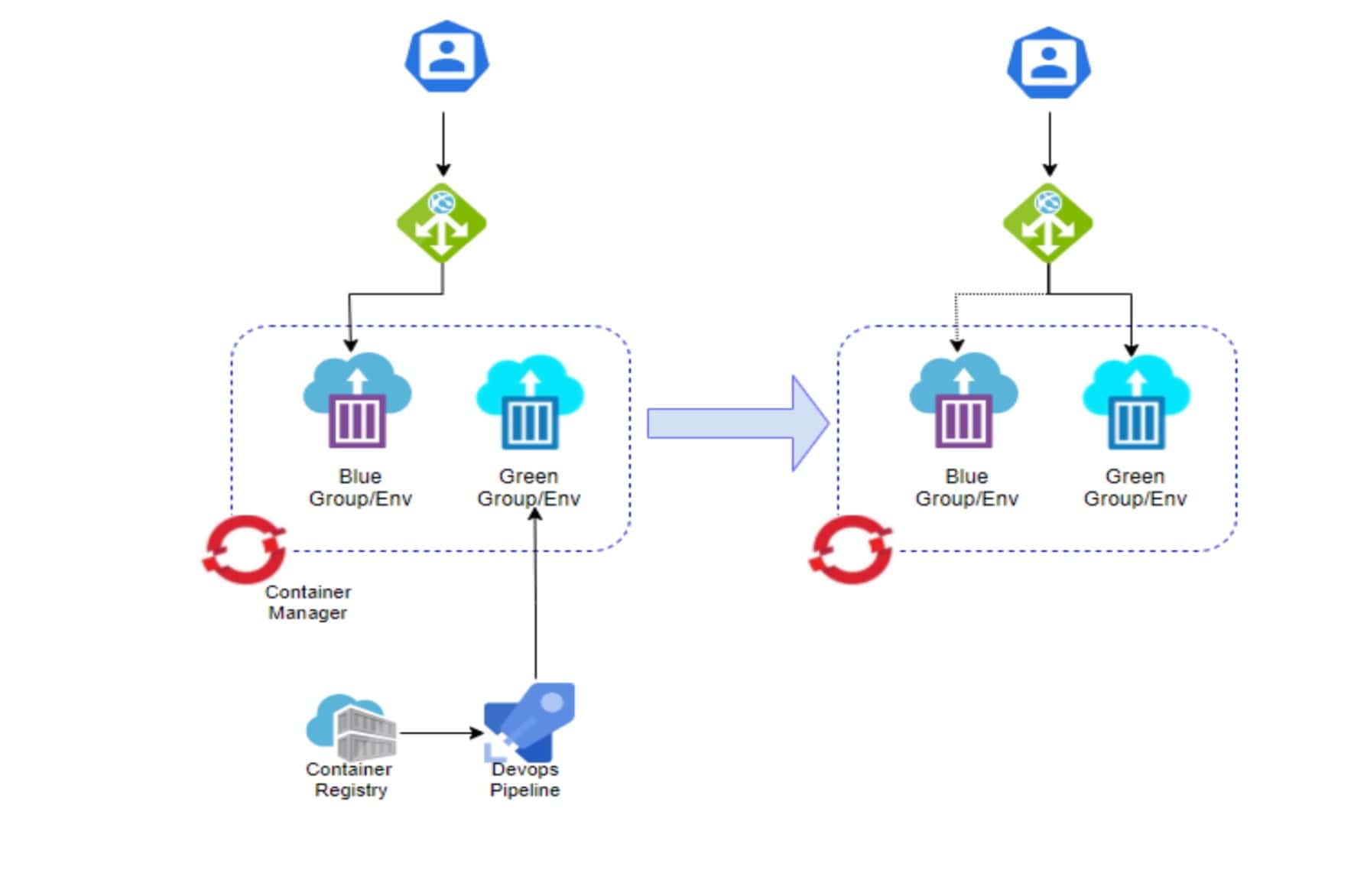
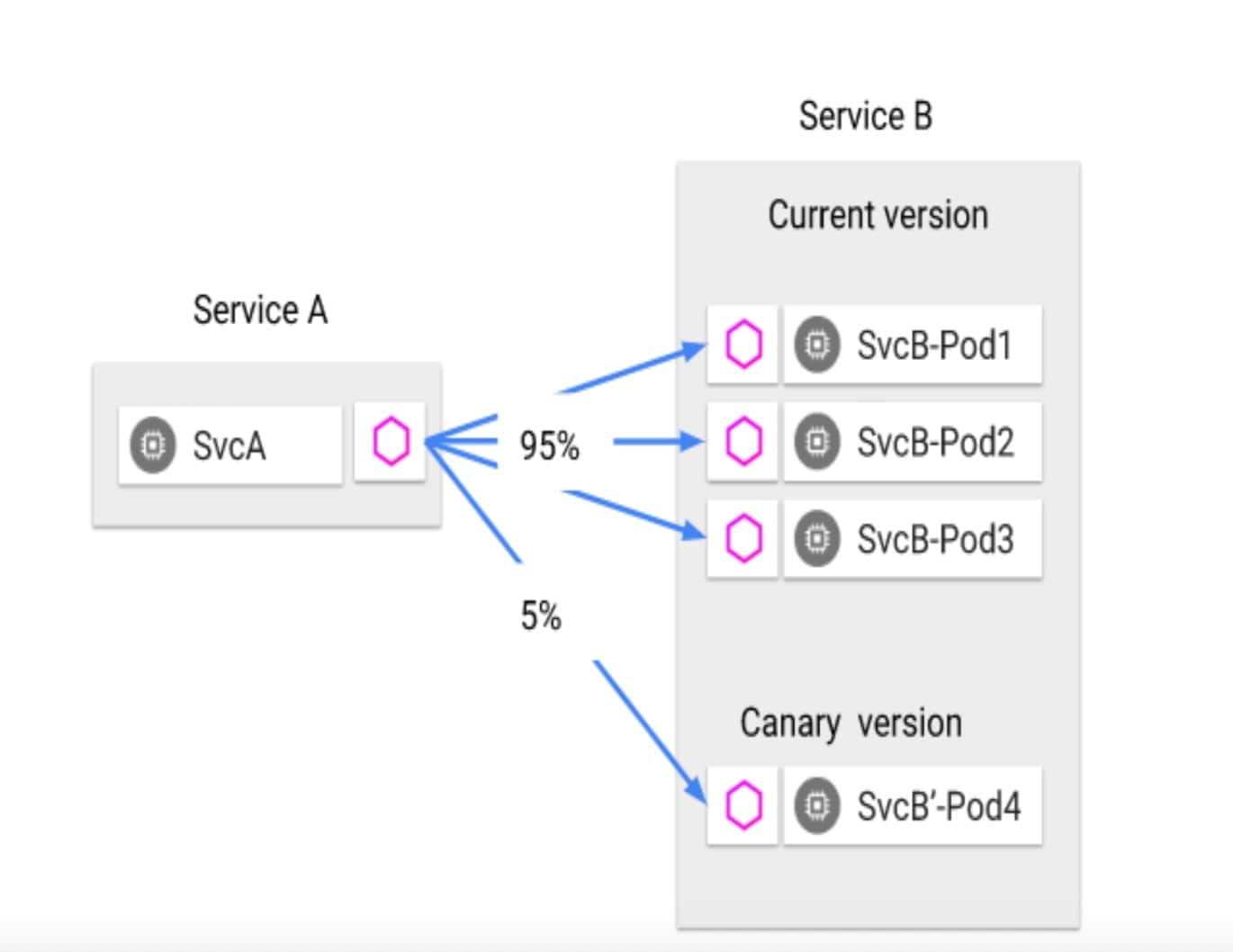
- The team implemented high availability and scalability using a combination of Kubernetes liveness, readiness, and startup probes, with Istio’s VirtualService & VirtualDestination rules. After a few non-200 responses traffic to the specified POD is automatically re-routed.
- Despite frequent production deployments and constant software upgrades driven by business requirements, Istio’s blue/green deployment support ensured seamless operation with minimal downtime and allowed the business to address potential bugs before releasing to a larger audience.
Enhanced Observability
- Istio’s Kiali dashboard provides detailed monitoring of application traffic through a user-friendly GUI
- Jaeger integration enables granular API monitoring across multiple microservices with traces and spans
- ELK stack implementation along with AppDynamics integration delivers detailed dashboards and robust alerting
From In-House Application to $300M Product
“This implementation with its zero trust architecture, seamless integration of new services, and ability to modify existing capabilities with zero downtime made our jobs much easier. We appreciate all the efforts made.” – DevSecOps Team Infosys Ltd. Client
The product received global acceptance and appreciation for its ease of use and availability. The team processed billions of dollars in transactions on time without any failures, benefiting the client. After marketing the product, the client secured deals with other investment banks worth $300 million USD. What started as an in-house application became a product that generated 10x more revenue than anticipated.
Built as a greenfield product, it leveraged existing personal banking, loan, mutual funds, and custody applications to give management a unified picture of NAV (Net Asset Value). The entire source code, build, and deployment activities were brought under Enterprise Agile/DevSecOps standards.
Key Impacts Include:
- Eliminated Silos: This application eliminated many silos implemented decades ago, saving costs and enabling faster time to market.
- Faster Decision-Making: The business can see the NAV in real time, enabling faster decision making.
- Financial Benefit: This is marketed as a product, and the customer realized a significant benefit.
- Global Impact: This application is used by the customer’s team across the globe and it has resulted in a 40% increase in efficiency.
- Efficient Operations: With high observability, there is a 40% savings in operations cost.
- AI Automation: With the fast adoption of AI agents there is future scope for cost reductions and faster time to market.
- Secure Platform: Despite being used by internal users and later marketed as a product there have been zero security incidents.