Problem statement
Confidential computing technologies such as Intel TDX and AMD SNP rely on hardware-controlled Roots of Trust (RoT), inherently binding remote attestation to specific CPU vendors. While these solutions offer strong security guarantees, they also introduce challenges for enterprises seeking compliance, transparency, and independence in managing their Trusted Execution Environments (TEEs). This raises key questions:
- How can organizations leverage TEE security features (e.g., memory encryption, attestation) without being fully dependent on vendor-controlled RoT?
- Is it possible to partially decouple the RoT while maintaining robust security guarantees?
Scenario
Consider a large enterprise deploying Intel TDX or AMD SNP servers, but with a requirement that the Root of Trust (RoT) be shared with a third-party authority—such as an internal certificate authority (CA) or an industry-wide trust anchor—to enable independent verification and operational flexibility. The goal is to retain the security benefits of TEEs while mitigating vendor lock-in.
Representative existing approaches
1. HyperEnclave
- Strengths:
- Fully vendor-agnostic and open-source.
- Utilizes TPM for attestation, minimizing reliance on CPU vendors.
- Considerations:
- Adopts an SGX-like, process-based isolation model, which, as of the time of this blog, may present compatibility challenges for integration with TDX/SNP ecosystems. (It is possible that HyperEnclave may support TDX in the future or may already have added support since the time of writing.)
- May require additional adaptation efforts for existing TEE workloads to leverage its architecture.
2. Azure vTPM
- Strengths:
- Facilitates partial decoupling of attestation through virtual TPMs in confidential VMs.
- Seamlessly integrates with mainstream confidential computing (CoCo) platforms.
- Considerations:
- Relies on Azure’s proprietary hypervisor and vTPM implementation, which may affect transparency and portability across different environments.
Our solution: Hybrid attestation with TPM and TEE integration
We propose a unified attestation framework that combines TEE-native reports (e.g., TDX/SNP attestation) with TPM-based quotes, enabling a shared RoT between hardware and third-party authorities.
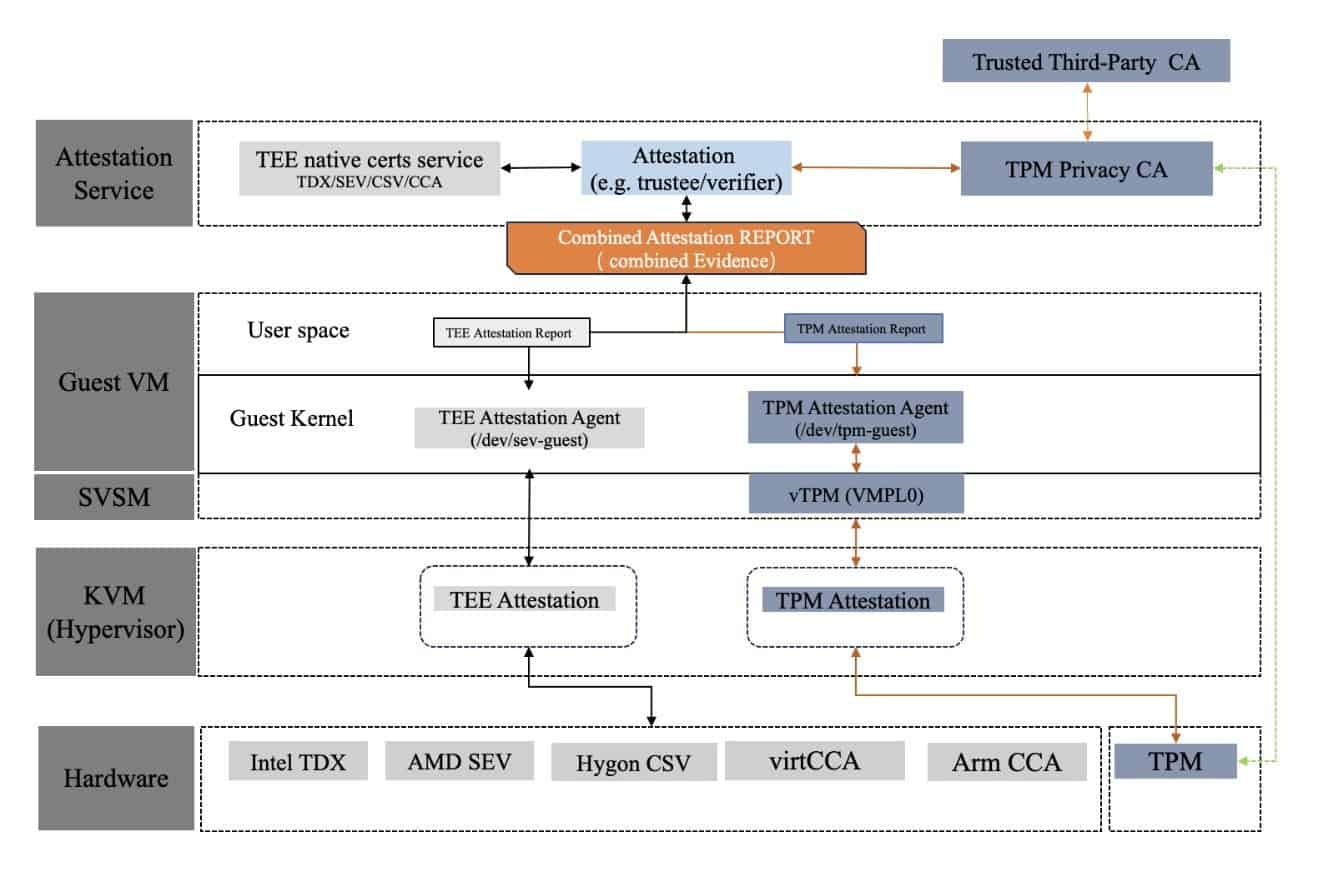
This solution presents a hybrid root-of-trust attestation framework for confidential computing environments, integrating both hardware-based Trusted Execution Environments (TEEs) and Trusted Platform Modules (TPMs), while supporting flexible certificate authority (CA) management.
Workflow overview
1. Deployment (registration) phase
- The physical TPM generates an Attestation Identity Key (AIK), which is securely stored within the TPM.
- The AIK private key remains protected and cannot be extracted from the TPM; only the public key is exported.
- The AIK public key is submitted to a Privacy CA, which issues an AIK certificate, establishing a trust anchor for subsequent attestations.
2. Runtime phase
- Each time a new Confidential VM (CVM) is launched, the vTPM instance running within the Secure Virtual Machine Monitor (SVSM) requests a certificate for its virtual AIK (vAIK) via a custom hypercall provided by the KVM hypervisor. This request is forwarded to the physical TPM, which collaborates with the Privacy CA to issue the vAIK certificate.
- The vTPM is responsible for trusted boot and integrity measurement of the CVM.
- Applications running inside the CVM obtain the vTPM Attestation Report through the/dev/tpm-guestinterface provided by the guest kernel.
- The guest kernel requests the vTPM to generate and return a vTPM Attestation Report for the CVM. This report is signed by the vAIK, providing cryptographic assurance of its origin and integrity.
- vTPM Integration:
- The virtual TPMs (vTPMs) run inside secure partitions:
- AMD SNP: Utilizes VMPL0 (highest privilege level) for isolation.
- Intel TDX: Leverages TD partitions for secure execution.
- The virtual TPMs (vTPMs) run inside secure partitions:
3. Verification phase
- The verifier checks the certificate chain: CA certificate → AIK certificate → vAIK certificate → vTPM Attestation Report.
- If the vTPM Attestation Report is valid and correctly signed, the verifier extracts the measurement values contained within the report.
- These measurements are compared against baseline images to confirm the integrity and expected state of the software environment.
4. Combined attestation approach
- TPM-based attestation and TEE-native attestation coexist within the architecture and do not conflict with each other.
- This joint attestation mechanism allows both TPM and TEE evidence to be collected, verified, and combined, providing enhanced security guarantees for both the hardware and software layers.
- The combined attestation report offers a comprehensive trust foundation, leveraging the strengths of both TPM and TEE technologies.
The architecture supports aggregation of TEE and TPM attestation evidence into a combined attestation report, providing comprehensive trust guarantees for both hardware and software integrity. This hybrid approach enables enterprises to flexibly manage root-of-trust anchors, enhance transparency, and support independent verification by trusted third-party CAs.In addition, our solution offers significant cost advantages. The TPM hardware modules required are highly standardized, modular, and inexpensive, making our architecture both practical and economical for large-scale deployment.
Implementation with Hygon CSV
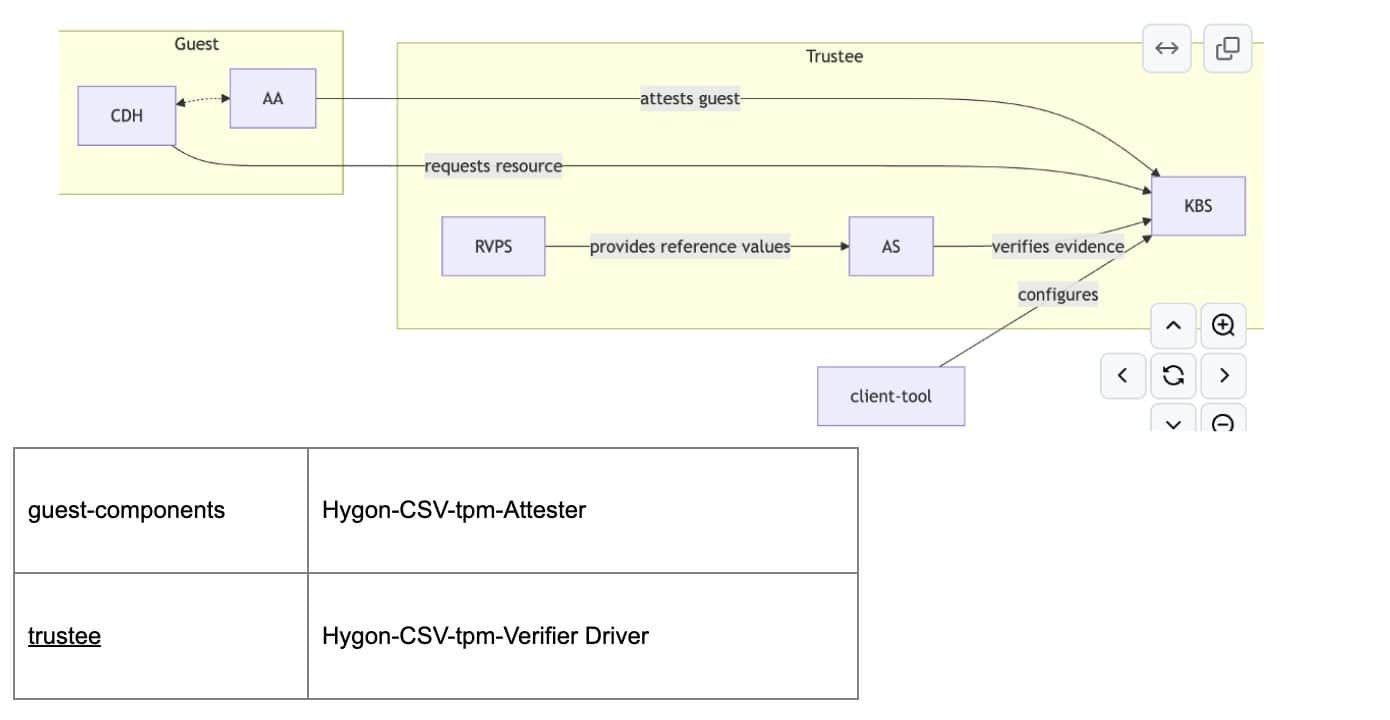
The current solution has been successfully developed and deployed in production on the Hygon CSV platform, where the first version is already supporting real-world applications. This implementation is based on the CoCo/trustee remote attestation framework, which provides the foundation for secure attestation and trust management. In addition, development efforts are underway to extend support to AMD SNP and Intel TDX platforms, further enhancing the versatility and coverage of this hybrid attestation architecture.
Advantages of the combined approach
- Vendor neutrality: RoT is shared between TEE hardware and a third-party TPM, reducing vendor lock-in.
- Customizable trust architecture: Provides organizations with the ability to define and manage their own TEE trust anchors and attestation mechanisms.
- Flexibility & scalability:The architecture is highly flexible and easily extensible, supporting integration with multiple hardware platforms and evolving security needs.
- Cost-effectiveness & large-scale deployment:By leveraging standardized and modular TPM hardware, the solution is low-cost and well-suited for economical, large-scale deployments.