This is post 2 out of 3 with an Introduction to Policy as Code preceding this.
Kubernetes continues to grow, but it has already become the main component of cloud native architectures. Maintaining your cluster is a crucial task, and solutions like Kyverno and OPA can be used to keep your cluster well maintained. Want to guarantee some observability-related labels? You got it. Need sidecars in your pods? You bet!
Together with the DevOps practices we mentioned in our prior post, you’ll also be able to identify and clean up any security or functional issues in your production!
In the last post we talked about the basics of Policy as Code and the overall idea around the concept. We passed through policy for general purpose as well as security-oriented, where teams use it to govern their environment using security best practices.
Today we’re going to talk about Policy as Code in the Cloud Native ecosystem, how it’s been used and the ecosystem’s most popular solutions.
Cloud Native PaC
When we get into CNCF’s landscape there’s a Security and Compliance section, where all security-related projects are listed.
In this list we have solutions like:
- IDPs (Identity Providers)
- Runtime Security
- Vulnerability Analysis
- Key, Secret and Certificate managers
All of them were accepted by CNCF and are maintained by Open Source contributors all over the world.

We also find in this section the Policy as Code solutions, used in our cloud native environments to keep them well-governed.
In this landscape, it’s worth mentioning:
- Kyverno: The founders of Nirmata created Kyverno for Kubernetes integration (that today does much more than just k8s), allowing engineers to enforce standards into Cloud Native environments. Using YAML for writing policies, engineers can create controls to not only audit their environments but to modify resources as well.
- OPA (Open Policy Agent): The founders of Styra created (and maintain) OPA, a Policy as Code solution that enables engineers to evaluate basically everything. By using Rego (OPA’s query language) users can implement any logic that needs to be evaluated when an event occurs (an event being anything that produces some kind of data). Using OPA, teams can implement custom controls, enforce personalized security guardrails and create authorization mechanisms that will take into consideration any kind of context passed by.
- Cloud Custodian: Created by Stacklet and mentioned in the first article of this series, Cloud Custodian is a Cloud Native solution that enables the enforcement of controls on Cloud environments (Azure, AWS and GCP). By using an “evaluator”, the solution will take in consideration the state of your current environment (and subsequent updates) and the written policies. Matching rules trigger the corresponding actions.
Those are all well-established solutions that can be used in your environment for a series of purposes. If you want to protect your assets, guarantee the quality and protection of your environment and do everything in a governed way, Cloud Native PaC is the way to go!
PaC in Kubernetes
We cannot talk about Cloud Native without talking about Kubernetes. Being one of the pillars of a Cloud Native architecture, the biggest companies in the world are running their solutions in Kubernetes clusters.
As companies scale their Kubernetes usage it’s important to keep environments governed and compliant with the best security practices available.
However, this becomes harder as clusters span multiple cloud providers, regions and will probably be of responsibility of different teams. A standardized way to protect these clusters is essential – and that’s where Policies as Code can help.
Using Kyverno, security teams can ship their policies to Kubernetes clusters using pipelines and IaC “recipes”. Security engineers can create policies, submit them to an evaluation process and push it to code repositories, where their versions will be maintained and can be used to rollout to older versions.
Let’s take as an example a Pod definition file. One commonly overlooked security aspect of pods is the Security Context configured by that object. Wrongfully configured, this setting can lead to Privilege Escalation, Root-like access to the Host and Access to File Systems.
To guarantee your pods are created with the correct security context, we can use a Kyverno policy to verify all deployments being applied into the cluster comply with the configurations determined by the organization.
The policy shown below can be seen on Kyverno Playground, it verifies the securityContext setting inside the Pod configuration. The result of this policy is given once a resource definition file is validated and provided as a Pass or Fail.
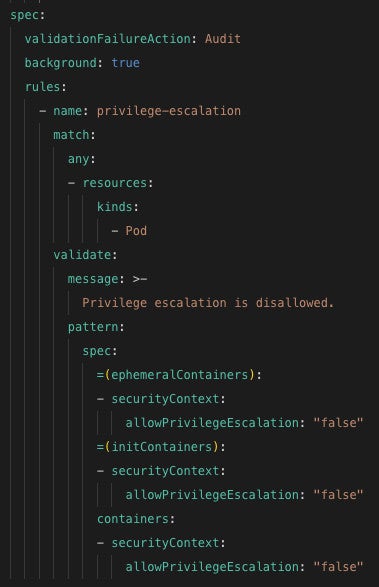
Installing Kyverno on a Kubernetes cluster will create its Admission Controller, the component responsible for validating and mutating resources as they are deployed to the cluster. Once your policy is written and applied to the cluster, all objects will go through the validation phase. New objects won’t be created if they are not compliant to the required standards and new objects might be evaluated if desired (this needs to be explicitly configured, otherwise existing objects will be left the way they are at the moment of configuration).
Automated Governance Maturity Model
With the purpose of helping companies on their Cloud Native Security and Policy as Code journey, the CNCF TAG Security developed a Maturity Model that outlines expected outcomes of well executed PaC implementation projects. Companies will benefit from it in the following ways:
- Understand the purpose and what to do with the available solutions.
- Specify the maturity level inside organizations regarding policy usage.
- What can be done regarding specific subjects using policies.
The document is about way more than just Policy as Code, it approaches a whole security model and culture inside companies, helping readers understand their gaps and enhancement opportunities. It talks about security integrated into DevOps practices, relationship between engineering teams and the whole process of governing a technology landscape inside an organization.
While going through it you’ll be able to assess your company’s environment in an understandable way, having at the end of the process a score that determines in which scale of maturity your architecture is.
With the four categories being Policy, Evaluation, Enforcement and Audit we can understand at which of those steps the bigger gaps are, identifying them and possibly other issues related to those subjects.
Getting to know more about the Cloud Native PaC Landscape
The possibilities within the Cloud Native Security Landscape are huge and there’s always a tool you can use for most use cases. With this idea in mind and having mentioned a couple of solutions earlier in this article, we would like to provide you with a couple of resources to make your life easier and help you in your PaC journey!
Kyverno Playground – https://playground.kyverno.io/#/
- Test existing policies into a web environment.
- Create your own policies using templates as base.
OPA Playground – https://play.openpolicyagent.org/
- Test existing policies into a web environment.
- Code your own authorization and validation policies.
- Validate your outputs against the policies using a data sample.
Semgrep Playground – https://semgrep.dev/playground/new
- Create App Sec rules and policies easily using the UI
- Validate your rules by running tests on local code samples or on GitHub.
Youtube videos:
- Kyverno for beginners (KodeKloud) – https://youtu.be/MxGAuVsJBXE?si=okkC52bc-f8xlMJR
- Kyverno playlist (Nirmata, the creators of Kyverno) – https://youtube.com/playlist?list=PLgEqb619wcz-56b1PEctELLtNTYGdb2NP&si=AY5gGGRldWpCl2yy
- OPA Intro & Deep Dive (KubeCon + CloudNativeCon EU 2024) – https://youtu.be/hENwFyrtm1g?si=XAJLJ1B6ltalngO2