This blog post contributed by Zach Jory, Head of Marketing of Aspen Mesh.
One of the challenges of developing and securing microservice-based applications in large teams is that services are often developed with different languages and frameworks. Service mesh overcomes these polyglot challenges by moving various aspects of microservice authentication and authorization to a common infrastructure layer.
There are various architectural options available to developers for securing microservices both with and without a service mesh. We’ll focus on how you can leverage a service mesh to simplify how you secure your microservices.
Service mesh helps ease microservices security with three distinct capabilities
- Authentication
- Authorization
- Zero Trust
Authentication
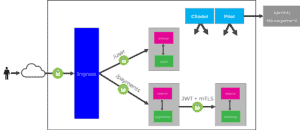
A service mesh provides the ability to do authentication between your services to ensure traffic flowing in your clusters is secure. There are 4 different authentication options available with a sidecar service mesh:
- JWT Validation in Applications
- JWT Validation at Ingress
- Istio Ingress TLS passthrough + JWT Validation at Sidecars
- Istio mTLS + JWT Validation
Authorization
A service mesh provides the ability to enforce service-to-service and end-user-to-service authorization. Using a service mesh for authorization can provide the ability to secure your services, and enforce the principle of least privilege. There are two authorization types that can be enforced with a service mesh:
- Role Based Access Control (RBAC)
- Attribute Based Access Control (ABAC)
Zero Trust Network
A service mesh allows you to enforce a zero trust network through a default stance of trusting nothing and verifying everything. Features such as mTLS, RBAC and certificate rotation make it easier to create a zero trust network.
If you want the details on how you can use a service mesh to more easily secure your microservices, check out the below presentation.